March 22, 2023
Facebook Ads is the advertising platform of the social network Facebook that promotes products and services through publications or ads of text, image or video. Since it’s operation is simpler than that of search engine advertising, it has become a tool widely used by small businesses looking for limited promotions geographically and over time.
However, they are also used by cybercriminals to spread malware such as InfoStealers through phishing scams, oftentimes in the form of an email. An Information Stealer (or InfoStealer) is malicious software designed to steal victim information, including usernames and passwords, which it sends to another system either via email or over a network.
The sections that follow chronicles a firsthand account of Nexusguard‘s hands-on-process, findings and experience with the latest malware campaign targeting unsuspecting Facebook users.
On February 18, 2023, while browsing Facebook, researchers at Nexusguard stumbled across a sponsored advertisement introducing the Windows PC version of ChatGPT as shown in Figure 1.
Figure 1 - Fake ChatGPT Facebook Advertisement
The ad prompted the user to download a purported ChatGPT version for Windows and redirected the user to hxxps[:]//openai-pc-pro[.]online, a fake Chat GPT website, which appears identical to ChatGPT's official website (Figure 2).
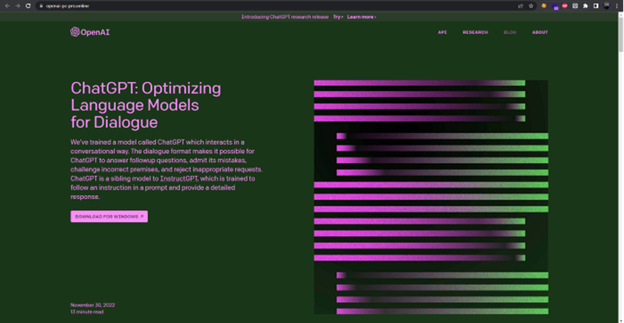
Figure 2 - Fake ChatGPT Website
The fake ChatGPT website also contained a download link which directed users to the URL shortener hxxps[:]//rebrand[.]ly/qaltfnuOpenAI. Threat actors use URL shorteners to either bypass certain filters on social media platforms or to simply hide the original link. Expanding the shortened URL produced a gzip archive with filename ChatGPT-OpenAI-Pro-Full-134676745403.gz containing an executable file with filename ChatGPT-OpenAI-Pro-Full-134676745403.exe.
In order to ascertain whether or not the URL was malicious, the executable file was uploaded to and run through VirusTotal by our team. Surprisingly, only 1 out of 68 vendors detected it as being malicious.

Figure 3 - URL Check using VirusTotal
We subsequently fired up a Windows VM to examine the executable file. Upon executing the file, it spawned subprocesses namely, Conhost.exe and reg.exe (Figure 4), added an entry to HKU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run for persistency. (Figure 5), and performed a DNS query on the domain cloudimagesv.top (Figure 6).

Figure 4 - Process tree showing subprocesses

Figure 5 - Registry key added for persistency

Figure 6 - DNS query attempted by the malware
The malware also tried to steal browser sensitive information (Figure 7), eventually sending data to 45.80.128.71 on port 443 (Figure 8).

Figure 7 - Malware tried to access browser stored data

Figure 8 - Malware attempted to communicate with C2 server
The behaviour of the malware is very similiar to that of RedLine Stealer. RedLine Stealer is malware available on underground forums which harvests information from browsers such as saved credentials, autocomplete data, and credit card information. A system inventory is also taken when running on a target machine, to include details such as the username, location data, hardware configuration, and information regarding installed security software. More recent versions of RedLine added the ability to steal cryptocurrency. FTP and IM clients are also apparently targeted by this family, and this malware has the ability to upload and download files, execute commands, and periodically send back information about the infected computer.
IntelX.io, a data aggregator of data leaks can provide a glimpse of how rampant RedLine Stealer is among agencies. Take note of the dates and times in Figure 9.

Figure 9 - Search results from Intel.X
A sample log from a RedLine Stealer infection is shown in Figure 10. (Credentials redacted)
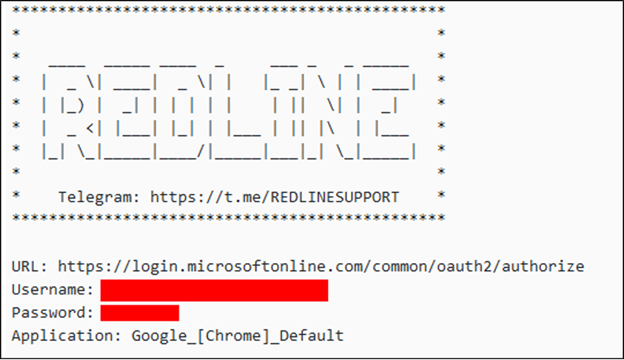
Figure 10 - Sample Redline log showing exfiltrated credentials
Examples of documents stolen by RedLine Stealer are shown in Figure 11.

Figure 11 - List of files exfiltrated by Redline Stealer
Conclusion
In sum, our findings highlight how cyber attackers are leveraging social engineering techniques to exploit the trust that users place in popular social networking services. It is important for users to understand that, just because a service appears to be legitimate, it is not always the case. With cybercriminals becoming increasingly sophisticated in their tactics, users must remain vigilant, stay informed and take proactive measures to safeguard their personal information and online identity.
Nexusguard not only develops threat intelligence by gathering and analyzing data about the latest malware threats, but also provides web and network application security solutions that can detect and block malware traffic, including those that target Facebook ads, helping organizations stay ahead of the curve and identify new attack techniques before they become widespread. For continuous visibility into your cyber risk, visit Nexusguard for more information.


