February 15, 2023
The global VoIP market is growing significantly with the increase of penetration of VoLTE networks and surge in VoIP traffic, leading to Session Initiation Protocol (SIP) becoming a de-facto protocol for Voice-over IP (VoIP) communication. SIP is an application layer protocol for creating and terminating sessions with one or multiple participants. Due to lower costs, large amounts of international traffic can be transmitted through SIP interfaces compared to traditional interfaces, allowing operators to move from conventional services to SIP-based services.
However, SIP is vulnerable to several types of attacks due to its open nature and lack of a clear defence line against the increasing spectrum of security threats. Among these threats, flooding attacks, known for their destructive impact, target SIP servers, resulting in a denial of service in VoIP applications. Techniques employed by perpetrators include SIP network fingerprinting, DNS/Internet Reconnaissance and SIP Port scanning to carry out attacks.
What is a SIP Flood Attack?
In a SIP flood attack, the attacker overwhelms the victim VoIP server by sending a flood of fabricated VoIP requests from a wide range of IP addresses in a short period. The victim server has to process the fake requests together with legitimate ones, which exhausts the CPU resources of the server, ultimately rendering it unavailable.
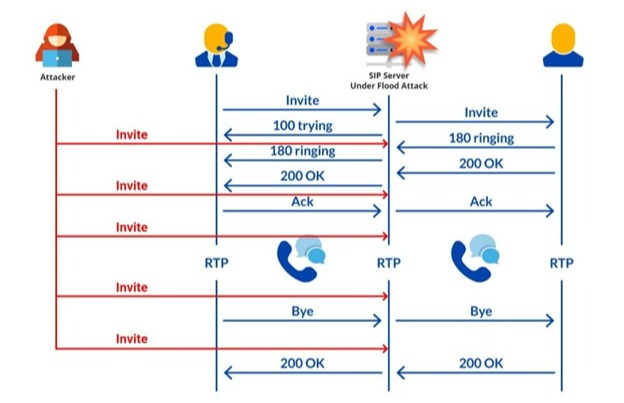 Figure 1 - SIP server overwhelmed by a flood of fabricated VoIP requests from a cyber attacker
Figure 1 - SIP server overwhelmed by a flood of fabricated VoIP requests from a cyber attacker
SIP Flood Protection using Nexusguard Services
Integral to its DDoS attack mitigation services, Nexusguard offers unique proprietary mitigation solutions that protect against all types of flood attacks.
Origin Protection (OP)
Nexusguard Origin Protection bolsters its capability against state exhaustion attacks by adding a new anti-SIP flood policy to its growing array of mitigation templates. This reinforcement not only prevents target server SIP connections from being impeded, but when coupled with flow control during SIP session establishment, also assures high server availability.
 Figure 2 - SIP Flood Protection using Nexusguard OP
Figure 2 - SIP Flood Protection using Nexusguard OP
Application Protection (AP)
As with OP, the addition of an anti-SIP flood policy to counter state exhaustion attacks makes it possible for Nexusguard Application Protection to protect from SIP flood attacks at scale without added latency, making it a perfect solution for enterprises and VoIP service providers. And with flow control implemented during SIP session establishment, server availability is guaranteed at all times.

Figure 3 - SIP Flood Protection using Nexusguard AP
Through a multi-layered security mechanism applied only to suspicious traffic, Nexusguard’s services protect networks from outside attacks and abuse. Our unique proprietary deployment model not only introduces zero latency in peace time and minimal latency under attack, but also ensures all types of flood attacks are kept well at bay.
For further information, please read about Nexusguard’s Application Protection and Origin Protection services.


