August 27, 2020
Given the sophistication and complexity of DDoS attacks nowadays, traditional threshold-based detection methods are no longer effective nor reliable. The advances in artificial intelligence (AI) in recent years has given rise to the application of Machine Learning models to enhance DDoS attack detection. It is only through the use of ‘deep learning-based’ predictive methods to analyze large amounts of traffic data, that malicious attack patterns can be quickly identified and dropped.
Nexusguard’s Smart Mode detection uses Machine Learning techniques to predict whether network traffic coming from a source is legitimate or part of a malicious DDoS attack. Compared to traditional threshold-based detection methods, it can identify more complex traffic patterns, and since it is an automated process, tedious manual configuration is greatly reduced.
The purpose of threshold-based detection is to determine whether the current traffic status of each host is normal or abnormal by analyzing the netflow traffic data in real time. An attack event will activate the L3 engine to protect the customer's network service by filtering out abnormal traffic.
Nexusguard’s Platform has two modes of operation:
- Normal
- Rapid
Both modes are based on thresholds. The detection engine calculates the traffic of each signature in real time and then compares them to a manually configured threshold. If the traffic signature is greater than that of the threshold, it will be treated as abnormal. The difference between the two methods lies in the time granularity; Normal Mode operates at the minute level, while Rapid Mode operates at the second level.
| Advantages | Disadvantages |
|
|
Rather than having to manually inspect large amounts of accumulated historical data, Nexusguard’s Platform harnesses and analyzes the data using Machine Learning models to help classify new incoming data or predict the next piece of data in a sequence. In the case of DDoS attack detection, the goal of the algorithm is to determine, on a scale of 0 to 1, how likely incoming traffic from a network is malicious. By analyzing masses of data, a well-trained learning model will be able to unravel convoluted characteristics of normal and malicious traffic that would have otherwise gone undetected to a human cybersecurity analyst.
Nexusguard’s Smart Mode uses machine learning algorithms to learn from historical netflow traffic data to detect whether the network is abnormal, i.e. under attack, and is automated to reduce customers’ manual configuration to a minimum. The current Smart Mode detection process can be divided into two steps:
- A machine learning model detects the status of netflow traffic each minute. The status can be normal or abnormal.
- An attack event is generated according to the netflow traffic status each minute. At present, if the status is abnormal for three consecutive minutes, an event is started. If the status is normal for 10 consecutive minutes, the current event is ended.
Smart Mode uses two machine learning models in step one. The detection process is illustrated below:
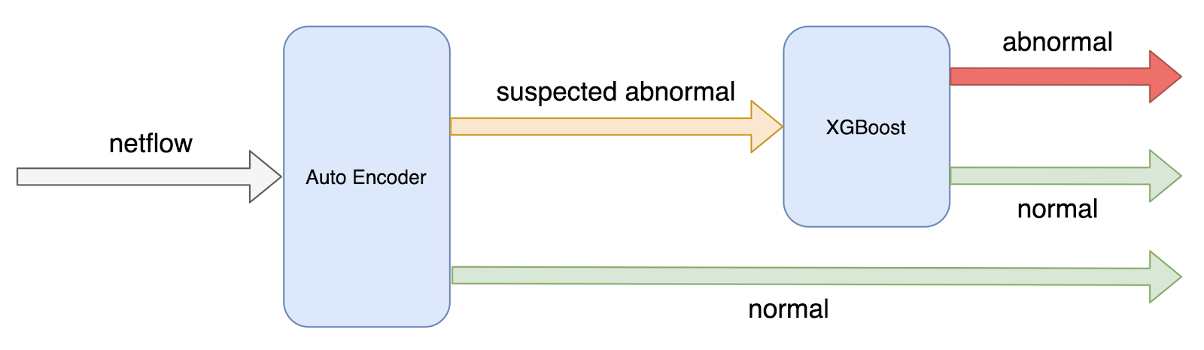
The advantages of Smart Mode are:
- Models used for detection can automatically learn from large amounts of historical data and real time data, and customers do not need to perform much manual configuration when using this mode.
- Models use many traffic variables; currently over 60 variables have been incorporated.
- Compared to the threshold-based method, it can identify more complex traffic patterns.
To evaluate the accuracy of Smart Mode, the current method compares mitigated traffic by Smart Mode with mitigated traffic of all customer networks.

In the histogram above, the blue bars represent the mitigated traffic by Smart Mode. The grey bars represent the mitigated traffic during an entire day for all customer networks, while the orange bars represent the mitigated traffic where the two coincide. Based on these promising findings, the use of Smart Mode detection bodes well for the future.
Disadvantages of Smart Mode:
Machine Learning is by no means the panacea for all DDoS issues, it does have shortcomings. Machine Learning relies heavily on data and if the data is not accurate, the effectiveness of the learned model will inevitably be poor.
Machine Learning models are very good at handling classification and predictive tasks, so long as the data is statistically similar to their learning models. But once they encounter new situations that vary from what they have previously learned, they can behave in unexpected ways. Although the use of Machine Learning to address the exponential threat of DDoS attacks is fast becoming a growing area of interest, it still requires a certain degree of human adjustment, but the overall results are very promising indeed.


